Research
My research confronts issues of security, privacy, and transparency in a broad range of computer systems and applications.
Some recent research themes:
Understanding SOC Phenomena
Modern Security Operation Centers (SOCs) deploy dozens of products so that analysts can monitor
the organization from different perspectives for evidence of attack.
Why, then, is news of another massive incident or breach a weekly occurrence?
This failure is the result of a constellation of
limitations in cybersecurity software that ultimately outsources the hardest work to the cognitive
capabilities of human analysts.
Recognizing SOC’s as complex sociotechnical systems, my recent work has attempted to directly measure SOC phenomena with the eventual goal of designing and validating effective interventions.
Recent Papers:
- Muhammad Adil Inam, Jonathan Oliver, Raghav Batta, and Adam Bates.
Carbon Filter: Scalable, Efficient, and Secure Alert Triage for Endpoint Detection & Response.
28th International Symposium on Research in Attacks, Intrusions and Defenses (RAID). Gold Coast, Australia. October 2025.
- Apurva Virkud, Muhammad Adil Inam, Andy Riddle, Jason Liu, Gang Wang, and Adam Bates.
How does Endpoint Detection use the MITRE ATT&CK Framework?
33rd USENIX Security Symposium (Security). Philadelphia, PA, USA. August 2024.
Detecting and Investigating Intrusions
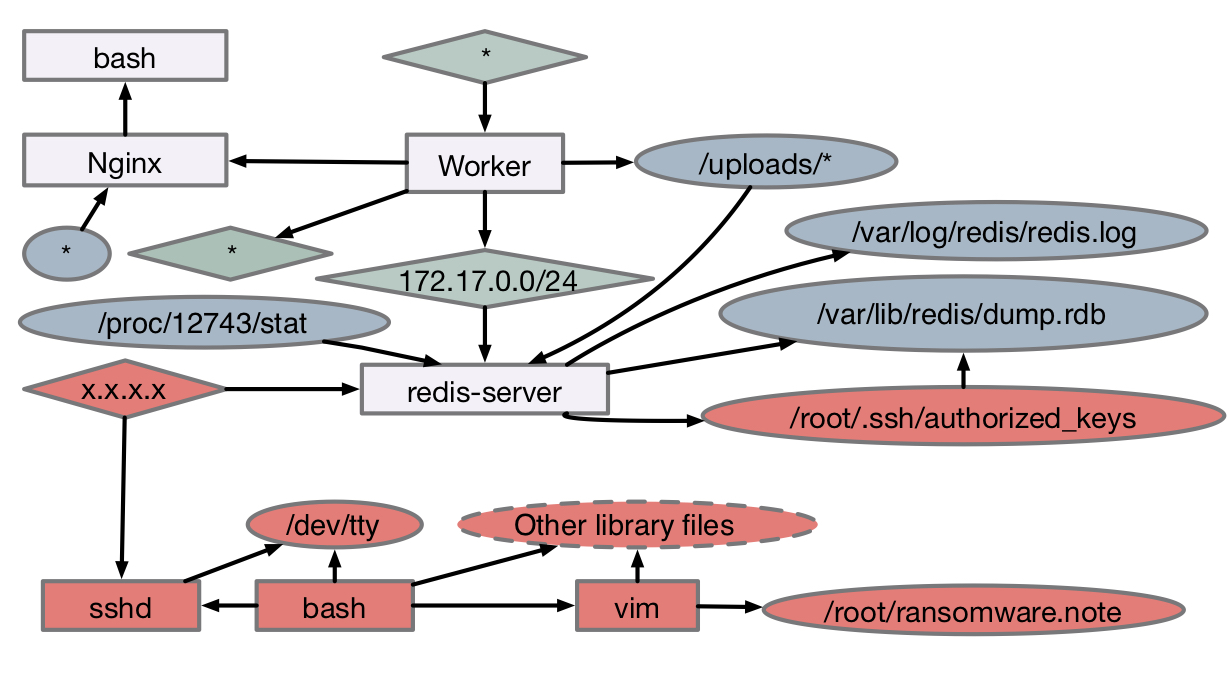
Our research also seeks to empower SOC analysts by improving the ways in which we audit computers,
allowing them to understand and react to attacks before serious damage is inflicted.
My earliest and ongoing contributions to this
space attempt to directly address the shortcomings of security products through provenance analysis.
Data Provenance is a transformation that can be performed on a time-series of
log events to surface causal interdependencies.
For endpoint events comprised of tuples,
processes and objects become vertices in a graph while operations become directed edges that
indicate the flow of information.
The graph can then be used to produce causal explanations
of inter-process workflows, such as identifying the root causes of an event. This straightforward
procedure is nonetheless revolutionary when applied to security operations, as today’s products
examine processes, endpoints, users in isolation without consideration for their interrelationships
Recent Papers:
- Jason Liu, Adil Inam, Akul Goyal, Andy Riddle, Kim Westfall, and Adam Bates.
What We Talk About When We Talk About Logs: Understanding the Effects of Dataset Quality on Endpoint Threat Detection Research.
IEEE Symposium on Security and Privacy (S&P). San Francisco, CA, USA. May 2025.
- Akul Goyal, Gang Wang, and Adam Bates.
R-CAID: Embedding Root Cause Analysis within Provenance-based Intrusion Detection.
IEEE Symposium on Security and Privacy (S&P). San Francisco, CA, USA. May 2024.
- Akul Goyal, Xueyuan Han, Gang Wang, and Adam Bates.
Sometimes, You Aren't What You Do: Mimicry Attacks against Provenance Graph Host Intrusion Detection Systems.
ISOC Network and Distributed System Security Symposium (NDSS). San Diego, CA, USA. February 2023.
- Muhammad Adil Inam, Yinfang Chen, Akul Goyal, Jason Liu, Jaron Mink, Noor Michael, Sneha Gaur, Adam Bates, and Wajih Ul Hassan.
SoK: History is a Vast Early Warning System: Auditing the Provenance of System Intrusions.
44th IEEE Symposium on Security and Privacy (S&P). San Francisco, CA, USA. May 2023.
Everyday User Privacy
Users are regularly asked to make choices that inform their digital privacy and even physical wellbeing.
Unfortunately, the significance of these decisions are rarely apparent to the user.
Worse, user's personal privacy needs are often at odds
with the incentives guiding the actions of developers, devices, and platforms
My research explores how these unforeseen security factors emerge through the mass proliferation of consumer
technologies such as Health & Fitness Tracking and the Internet of Things (IoT).
Beyond their technical contributions, these projects seek to inform public discourse
on privacy protections, bridging the technical and societal dimensions of data use.
Recent Papers:
- Yeeun Jo, Mahnoor Jameel, Camille Cobb, and Adam Bates.
"I’m not as afraid as a woman might be about sharing my exact location:" On the Intersection of Identity and Privacy Concerns in Fitness Tracking.
ACM CHI Conference on Human Factors in Computing Systems. Yokohoma, Japan. April 2025.
- Phoebe Moh, Pubali Datta, Noel Warford, Adam Bates, Nathan Malkin, and Michelle L. Mazurek.
Characterizing Everyday Misuse of Smart Home Devices.
IEEE Symposium on Security and Privacy (S&P'23). San Francisco, CA, USA. May 2023.
- Jaron Mink, Amanda Rose Yuile, Uma Pal, Adam Aviv, and Adam Bates.
Users Can Deduce Sensitive Locations Protected by Privacy Zones on Fitness Tracking Apps.
ACM CHI Conference on Human Factors in Computing Systems (CHI). New Orleans, LA, USA. April 2022.
Network & Communications Security
The global economy is dependent on the security of network communications and infrastructures. Unfortunately, these security properties are violated with alarming frequency due to implementation errors or developer confusion, or because systems are made use of in unanticipated ways. This research seeks to better understanding this breakdown between theory and practice, and identify ways to restore correct functionality in vulnerable networked systems.
Recent Papers:
- Isaac Polinsky, Pubali Datta, Adam Bates, and Will Enck.
GRASP: Hardening Serverless Applications through Graph Reachability Analysis of Security Policies.
The Web Conference (WEB). Singapore. May 2024.
- Pubali Datta, Isaac Polinsky, Muhammad Adil Inam, Adam Bates, and Will Enck.
ALASTOR: Reconstructing the Provenance of Serverless Intrusions.
USENIX Security Symposium (Security). August 2022.
- Benjamin E. Ujcich, Samuel Jero, Richard Skowyra, Adam Bates, William H. Sanders, and Hamed Okhravi.
Causal Analysis for Software-Defined Networking Attacks.
USENIX Security Symposium (Security). August 2021.