Research
My research confronts issues of security and transparency in computer systems and networks.
My major research thrusts are:
Detecting and Investigating Intrusions
Modern computing systems are sprawling and complex, creating many opportunities for would-be intruders
to break-in and remain undetected.
Attackers can now dwell inside of networks for months or years before being noticed, as evidenced by numerous
high-profile data breaches in the news.
Our research seeks to empower system defenders by improving the ways in which we audit computers,
allowing them to understand and react to attacks before serious damage is inflicted.
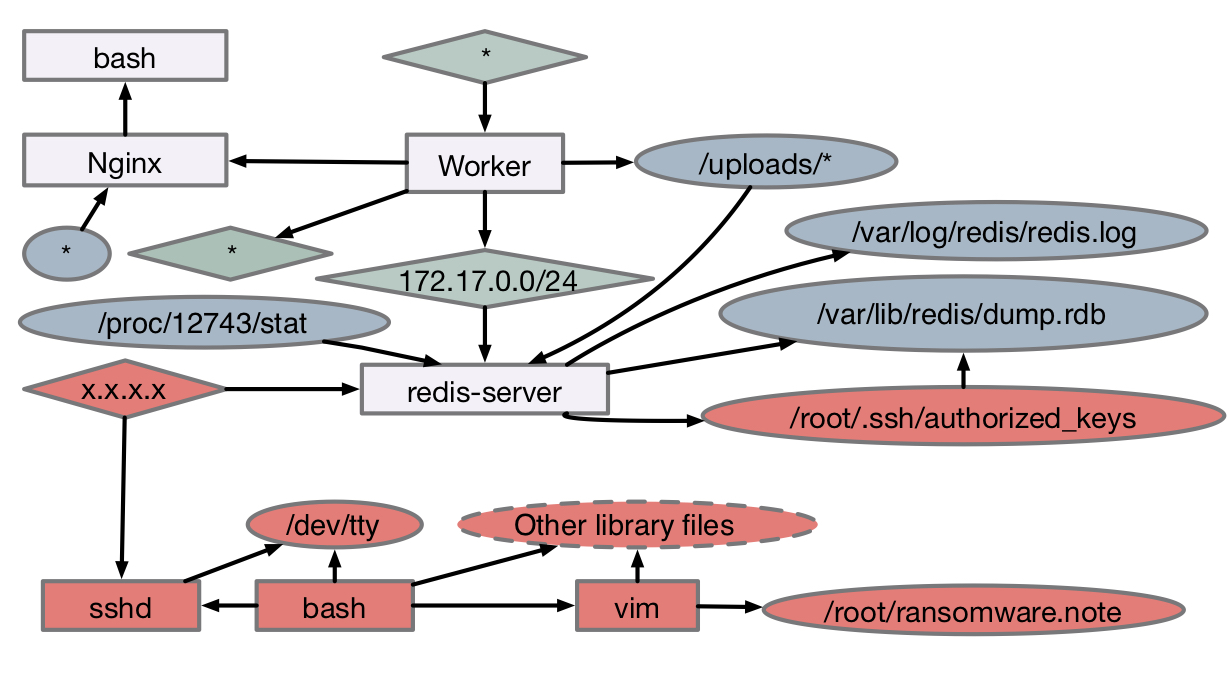
A key technique we leverage in this work isf data provenance, which iteratively parses low-level
events (e.g., Process A read File 1) into a causal dependency graph that describes the entire
history of system execution.
These graphs allow security analysts to identify the root causes of suspicious activities through causal analysis,
and can also be used to improve automated intrusion/anomaly detection systems.
Recent Papers:
- Muhammad Adil Inam, Wajih Ul Hassan, Ali Ahad, Adam Bates, Rashid Tahir, Tianyin Xu, and Fareed Zaffar. Forensic Analysis of Configuration-based Attacks. ISOC Network and Distributed System Security Symposium (NDSS), Februrary 2022.
- Carter Yagemann, Mohammad Noureddine, Wajih Ul Hassan, Simon Chung, Adam Bates, and Wenke Lee. Validating the Integrity of Audit Logs Against Execution Repartitioning Attacks. ACM Conference on Computer and Communications Security (CCS). November 2021.
- Riccardo Paccagnella, Kevin Liao, Dave (Jing) Tian, and Adam Bates. Logging to the Danger Zone: Race Condition Attacks and Defenses on System Audit Frameworks. ACM Conference on Computer and Communications Security (CCS). November 2020.
- Wajih Ul Hassan, Adam Bates, and Daniel Marino. Tactical Provenance Analysis for Endpoint Detection and Response Systems. IEEE Symposium on Security and Privacy (Oakland). May 2020.
- Carter Yagemann, Mohammad Noureddine, Wajih Ul Hassan, Simon Chung, Adam Bates, and Wenke Lee. Validating the Integrity of Audit Logs Against Execution Repartitioning Attacks. ACM Conference on Computer and Communications Security (CCS). November 2021.
Consumer Device Security
Spanning smart phones and the Internet of Things, consumer-oriented computing devices are diverse and pervasive.
While these technologies create unprecedented opportunity for innovation,
they also expose novel attack surfaces that must be better understood in order to provide adequate protection to end users.
Our work in this space is two fold:
first, to reason about the security challenges created by consumer devices,
but also to identify ways in which these technologies can be leveraged to address the broader goals of computer security.
Recent Papers:
- Carter Yagemann, Mohammad Noureddine, Wajih Ul Hassan, Simon Chung, Adam Bates, and Wenke Lee. Validating the Integrity of Audit Logs Against Execution Repartitioning Attacks. ACM Conference on Computer and Communications Security (CCS). November 2021.
- Qi Wang, Pubali Datta, Wei Yang, Si Liu, Carl Gunter, and Adam Bates. Charting the Attack Surface of Trigger-Action IoT Platforms. ACM Conference on Computer and Communications Security (CCS), November 2019.
- Wajih Ul Hassan, Saad Hussain, and Adam Bates. Analysis of Privacy Protections in Fitness Tracking Social Networks -or- You can run, but can you hide? USENIX Security Symposium, August 2018.
- Deepak Kumar, Riccardo Paccagnella, Paul Murley, Eric Hennenfent, Joshua Mason, Adam Bates, and Michael Bailey. Skill Squatting Attacks on Amazon Alexa. USENIX Security Symposium, August 2018.
- Qi Wang, Wajih Ul Hassan, Adam Bates, and Carl Gunter. Fear and Logging in the Internet of Things. ISOC Network and Distributed System Security Symposium (NDSS), February 2018.
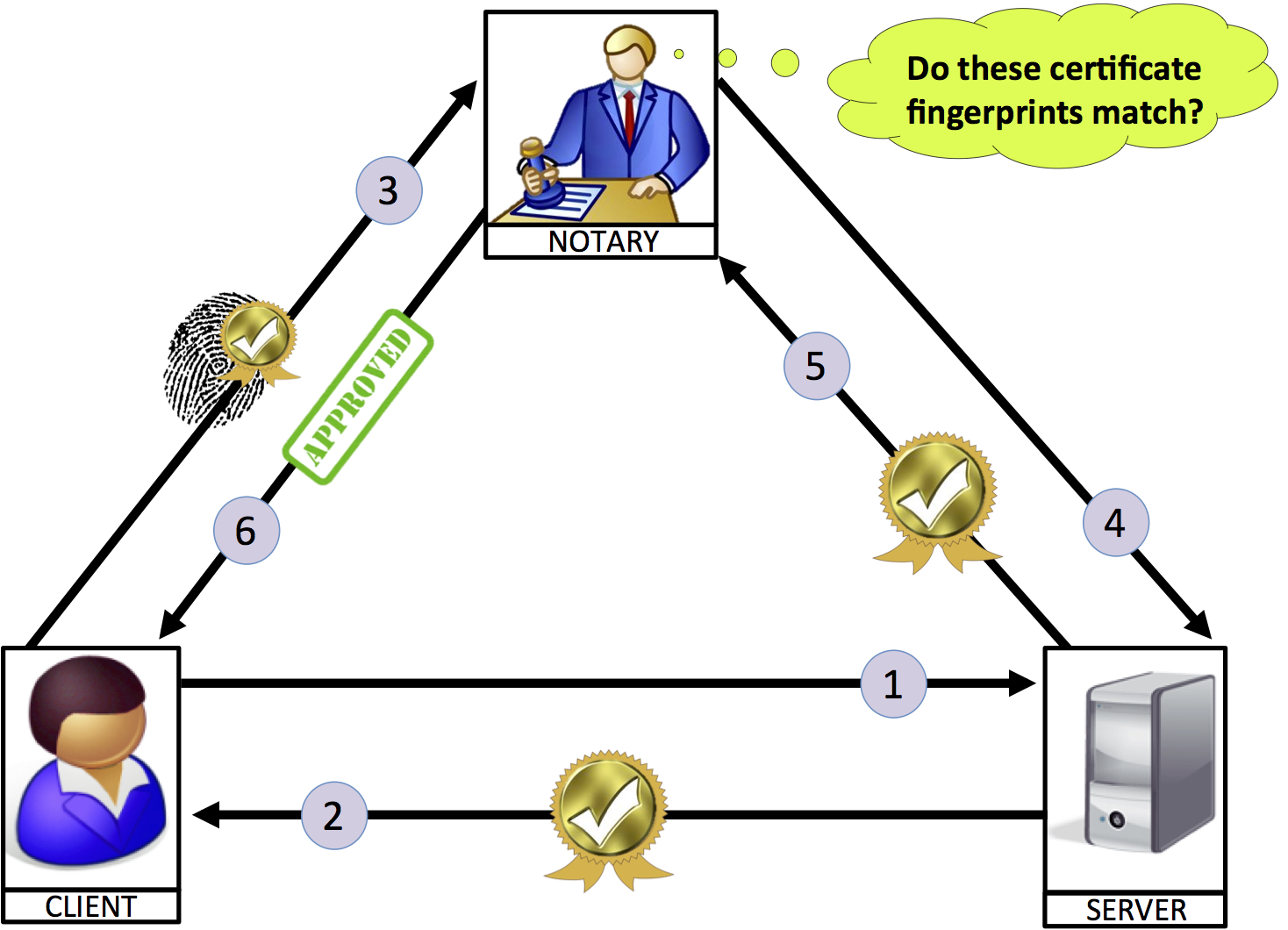
Network & Communications Security
An increasing proportion of the global economy is dependent on the security of network communications and infrastructures. Unfortunately, these security properties are violated with alarming frequency due to implementation errors or developer confusion, or because systems are made use of in unanticipated ways. This research seeks to better understanding this breakdown between theory and practice, and identify ways to restore correct functionality in vulnerable networked systems.
Recent Papers:
- Pubali Datta, Isaac Polinsky, Muhammad Adil Inam, Adam Bates, and Will Enck. ALASTOR: Reconstructing the Provenance of Serverless Intrusions. USENIX Security Symposium. August 2022.
- Benjamin E. Ujcich, Samuel Jero, Richard Skowyra, Adam Bates, William H. Sanders, and Hamed Okhravi. Causal Analysis for Software-Defined Networking Attacks. USENIX Security Symposium. August 2021.
- Arnav Sankaran, Pubali Datta, and Adam Bates. Workflow Integration Alleviates Identity and Access Management in Serverless Computing. Annual Computer Security Applications Conference (ACSAC). December 2020.
- Pubali Datta, Prabuddha Kumar, Tristan Morris, Michael Grace, Amir Rahmati, and Adam Bates. Valve: Securing Function Workfows on Serverless Computing Platforms. The Web Conference (WWW). April 2020.
- Benjamin E. Ujcich, Samuel Jero, Anne Edmundson, Qi Wang, Richard Skowyra, James Landry, Willam H. Sanders, Christina Rita-Notaru, and Hamed Okravi. Cross-App Poisoning in Software-Defined Networking. ACM Conference on Computer and Communications Security (CCS), October 2018.